
Security
Because our customers use our technology to move their most valuable assets on the Signiant Platform, we take precautions to secure every layer involved in file movement. Our security technology and implementation regularly undergo extensive third-party reviews to ensure effective protection.

Signiant’s TPN Gold assessment was conducted by Independent Security Evaluators (ISE), a TPN-accredited assessor with a long track record as a respected independent third-party technology evaluator in the media industry.

Signiant is SOC 2 compliant. SOC 2, developed by the AICPA, ensures that we adhere to stringent security, availability, processing integrity, confidentiality, and privacy standards. This certification assures our commitment to robust data security and privacy practices.
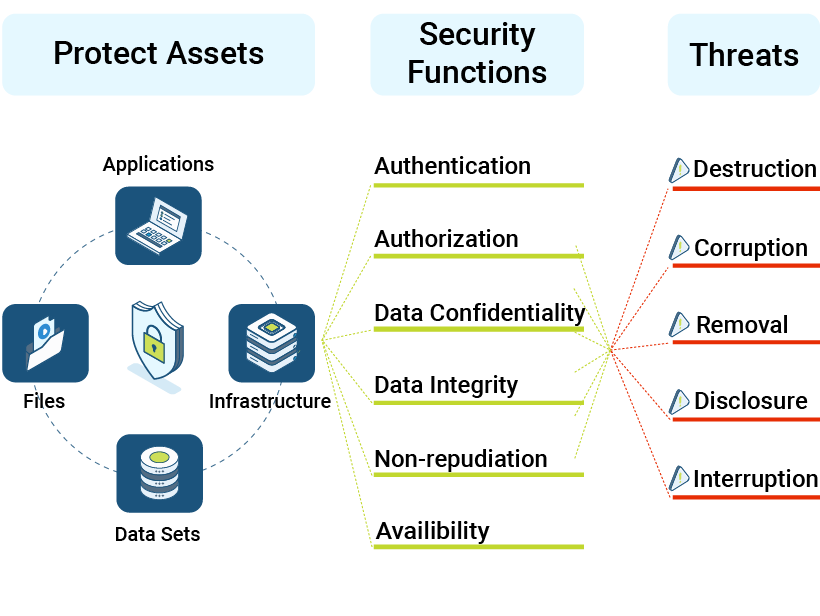
Signiant utilizes standards-based security technology like Transport Layer Security (TLS) to secure data and information as it is transmitted, including advanced authentication, data integrity, and data confidentiality.
We ensure that all transfers are appropriately authorized and tracked to provide irrefutable proof that files were delivered.
However, designing secure software is only half the picture. Operating a secure service is equally as important. As a SaaS provider, Signiant employs service organization controls implemented in accordance with industry standards and best practice.

Corbel 3D
“It’s just nice to have the assurance of Signiant. We have a platform that is trustworthy in the industry.”
~ Jingyi Zhang, CEO
Learn More About the Signiant Platform
The Signiant Platform builds on the foundation of our world-class fast file movement apps and adds workflow-centric production services that make working with media even more efficient.