Even with zero-day exploits on the rise, software updates remain critical

Earlier this month, the naturally paranoid among us could again claim some righteous vindication, at least in the area of software security. Two related zero-day vulnerabilities in Google Chrome and Microsoft Windows were discovered out in the wild, actively being exploited by malicious hackers.
It used to be that zero-day exploits (security vulnerabilities exploited before a security update has even been released) were considered rare by security experts, but that seems to be changing.
Back in February, Matt Miller of Microsoft’s Security Response Center gave a presentation on software vulnerability mitigation trends at Blue Hat. Their research indicates that zero-days have become far more common than non-zero-days (security vulnerabilities exploited within 30 days after a security update is available).
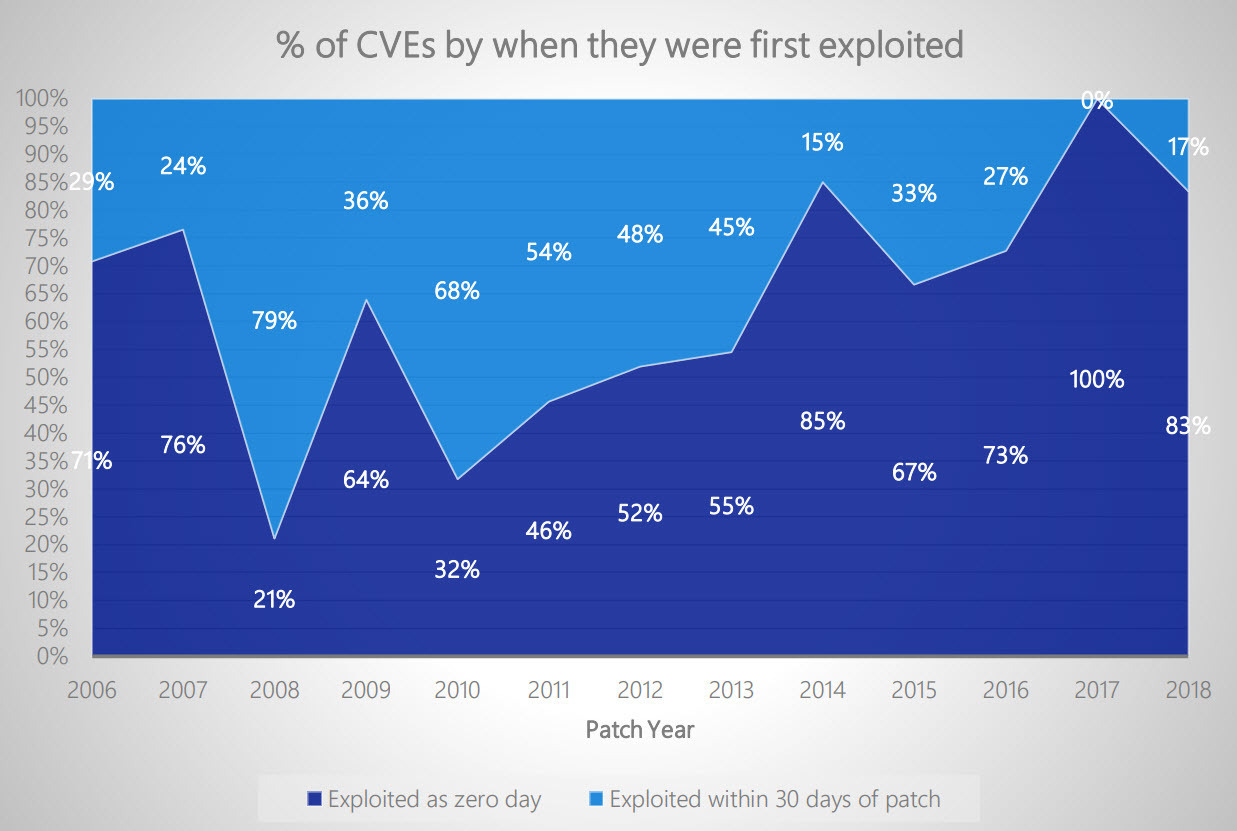
Credit: Matt Miller
But this data can be misleading, and not just because it’s Microsoft software specific. Taken out of context, the prevalence of zero-day exploits can make it seem like updating software with the latest security patches won’t make much difference.
However, many major enterprise breaches of the last few years have resulted from a lack of updating software in a timely manner, such as the preventable Equifax data breach of 2017, which impacted 143 million Americans.
Furthermore, the solution to both zero-day threats on Chrome and Windows is still to update your software. Google issued a release to address the threat and urged users to make sure it was implemented. And Microsoft emphatically encouraged users to update to Windows 10, with Clement Lecigne saying, “we strongly believe this vulnerability may only be exploitable on Windows 7 due to recent exploit mitigations added in newer versions of Windows.”
Signiant Security: On-prem and SaaS solutions
Signiant is a recognized leader in media technology security, winning the DPP ‘Committed to Security Mark’ for both broadcast and production. Part of our security strategy is to employ third-party security firm Independent Security Evaluators (ISE) to extensively review our security technology and implementation. A bit of wisdom offered by Shane Lester, a security analyst with ISE:
“It is important to update software to help prevent software vulnerabilities that your manufacturer is already aware of. Some software updates provide details about the issues that are fixed that can often provide attackers with ammunition when targeting users with poor updating practices.
For example, attacks using Heartbleed were seen the day after the patch was available. Even a month later, it was reported that between 1 and 2 percent of the most popular 800,000 websites were still vulnerable.
Software update management is important in securing any system. After all, your system is nothing but a collection of software libraries working together as you try to maintain a secure computing environment.”
Bottom line, the complexity of cyber vulnerabilities is immense and scary, and the constantly adapting tactics of cyber actors is impressive and even scarier. Keeping software up to date is one thing you can do to mitigate them all.
Since we’re on the subject, if you’re a Manager+Agents user, be sure to update to version 13.5. It has some important security enhances and bug fixes, not to mention improved scaling, reliability, APIs, object storage and more.
For our Media Shuttle, Jet and Flight users, automatic updates — including security patches — are one of the great benefits of Signiant SaaS. With no down time, you may not even know they occurred, but it’s still good to keep in mind how important they are.


